Cyberattacks are malicious attempts to harm computer systems or networks. Regulatory pressure is rising for financial institutions to improve their cybersecurity practices. Most common types of cyber-attacks are..
- Phishing
- Spoofing
- Malware
- Identity based Attacks
- Insider threats
- DNS tunneling
- IoT Based Attacks
- Denial of Service attacks
Quick Links
What is Phishing?
This social engineering attack deceives victims into sharing personal information or downloading malware. Phishing attempts can come through various channels like email, SMS, phone calls, or social media.
Spear Phishing: Targets specific individuals or organisations with crafted emails to steal sensitive information or infect devices with malware.
Whaling: A high-level spear phishing attack targeting senior executives to steal money, information, or computer access for further attacks.
Smishing: Phishing via SMS. Attackers send fake text messages disguised as reputable companies to trick victims into sharing personal information such as paaswords or credit card numbers.
Vishing: Phishing attacks done through phone calls and voice messages, impersonating reputable organisations to steal private information like bank details and passwords.
Two spoofing techniques
Domain Spoofing: Attackers create fake websites or email domains that closely resemble legitimate ones, tricking victims into trusting them. These often involve subtle differences in spelling or extensions.
Email Spoofing: Fraudulent emails are sent with forged sender addresses to appear legitimate. This increases the likelihood of recipients opening the mail and potentially clicking malicious links or attachments.
Malware:
It is a program or code that is created with the intent to do harm to a computer, network or server. Malware is the most common type of cyberattack, its subsets are ransomware, fileless Malware trojans, viruses etc.
Ransomware: Holds your data hostage by encrypting it, demanding a ransom for decryption. Spreads through phishing emails, vulnerabilities, and misconfigurations.
Fileless Malware: Launches cyberattacks using legitimate tools already on your device, making detection difficult. No additional files are installed
Identity-Based Attacks:
When a valid user’s credentials have been compromised and an adversary is pretend to be that user. For e.g., people often use the same user ID and password across multiple accounts.
Insider Threats:
When current or former employees that pose danger to an organisation because they have direct access to the company network, sensitive data, and intellectual property (IP), as well as knowledge of business processes, company policies or other information that would help carry out such an attack.
DNS Tunneling:
It hides malicious data within DNS requests, creating a secret path for attackers to sneak malware, steal information, or access a network.
IoT-Based Attacks:
It is a cyberattack that targets an Internet of Things (IoT) device or network. Once compromised, the hacker can assume control of the device, steal data, or join a group of infected devices.
Denial-of-Service (DoS) Attacks:
These attacks overwhelm a network with fake traffic, preventing legitimate users from accessing services. DoS attacks can disrupt business operations and cost time and money to resolve, but typically don’t steal data.
Stages of Cyber Risks
STAGE 1 Assessing the cyber risk : Identify common threats such as ransomware, phishing attacks, and insider breaches.
NEXT STAGE 2 Impact of cyber risk: Consider the potential consequences of a cyberattack, which could include financial losses, operational disruptions, reputational damage, fines and penalties.
STAGE 3 Managing the cyber risk: Develop a plan to understand your organisation’s risk profile, evaluate your current security measures, and implement controls to mitigate threats.
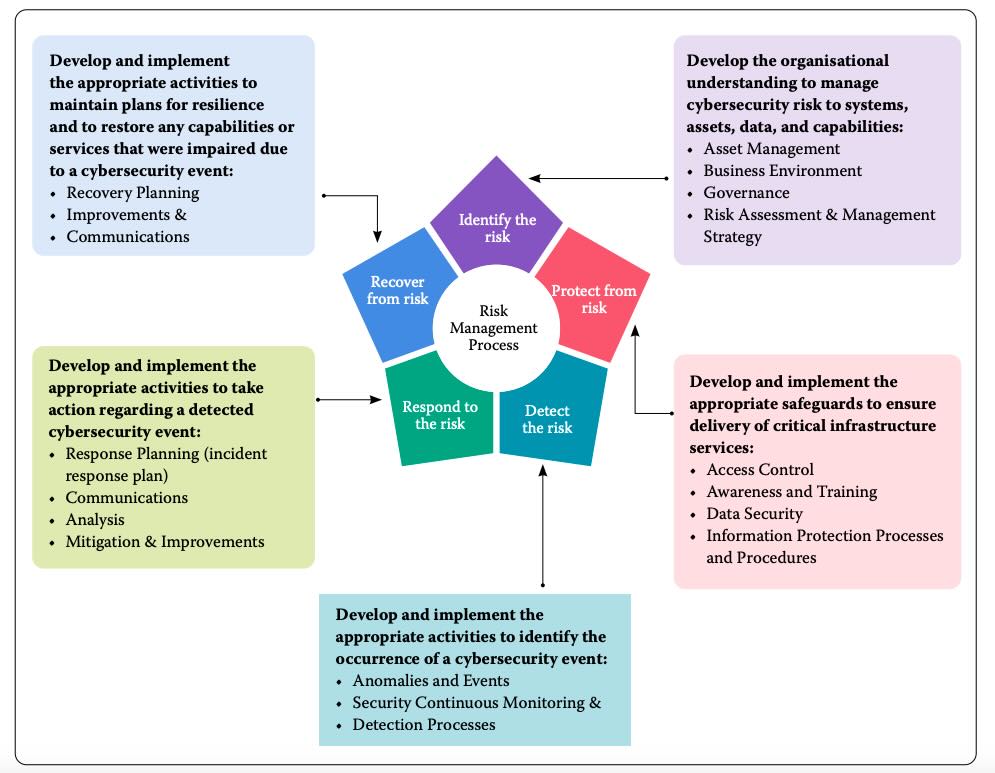
Cyber Security Framework
Cybersecurity framework includes how management is identifying the risk, protecting and safeguarding its assets (including electronic assets) from the risk. Management preparedness to detect the attacks, anomalies and responsiveness to the adverse event.